Unlock the Future: Passkey + DID + FIDO - Exploring the Next Generation of Digital Wallets and Identities
2023-05-29
Recommend Articles

Why Are We Hearing So Much About Stablecoins—and Why Does Taiwan Suddenly Matter?
What Do ISO 27001, ISO 27701, and SOC 2 Type 2 Actually Protect—and Why Should Companies Care?
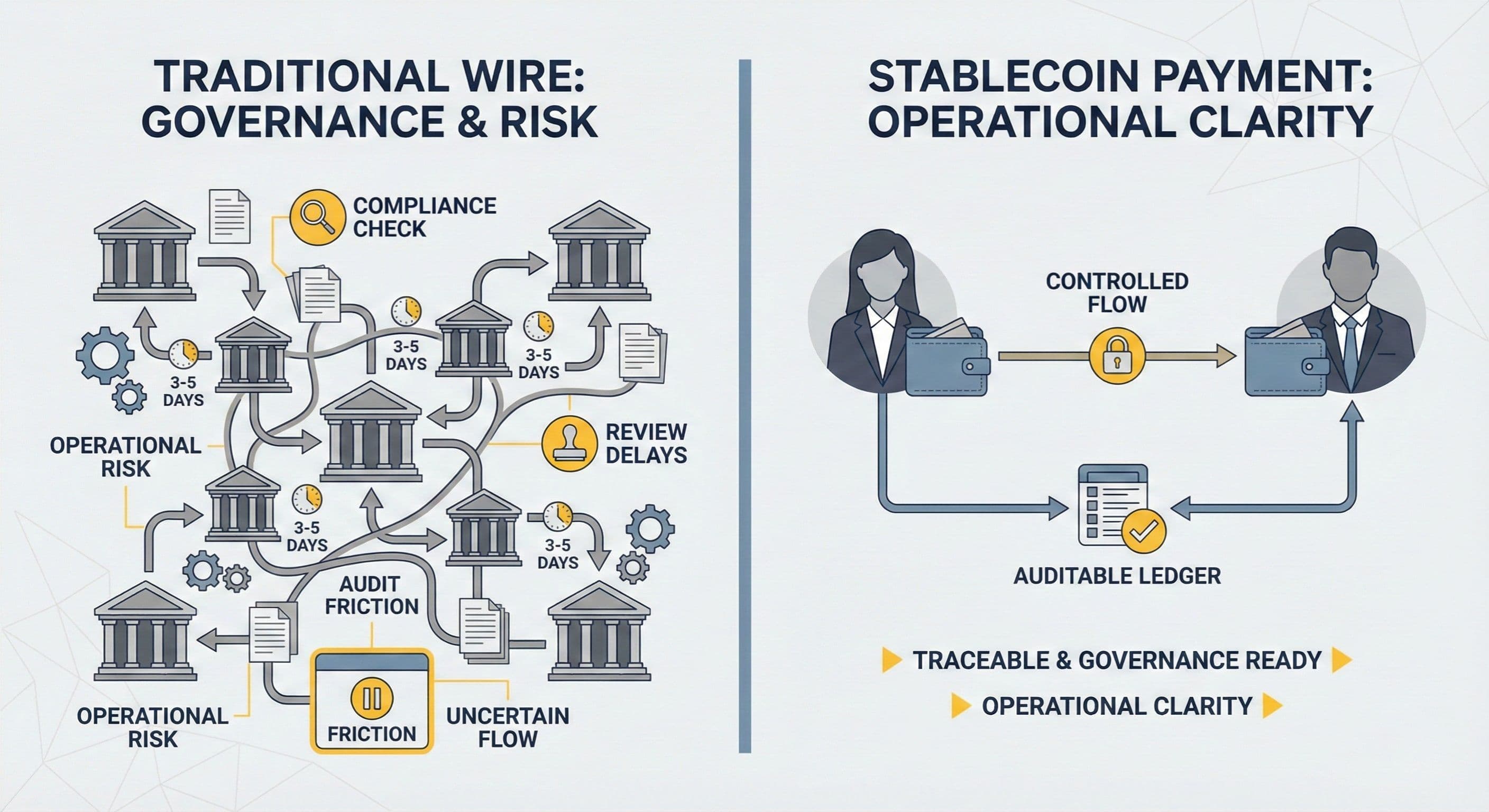
Cross-Border Wire Transfers vs. Stablecoin Payments: How Much Can Companies Actually Save—and At What Cost?
Hot Articles
Hot Tags
HotNewsNFTBlockchainDeFiSecurityComplianceUpdates






